
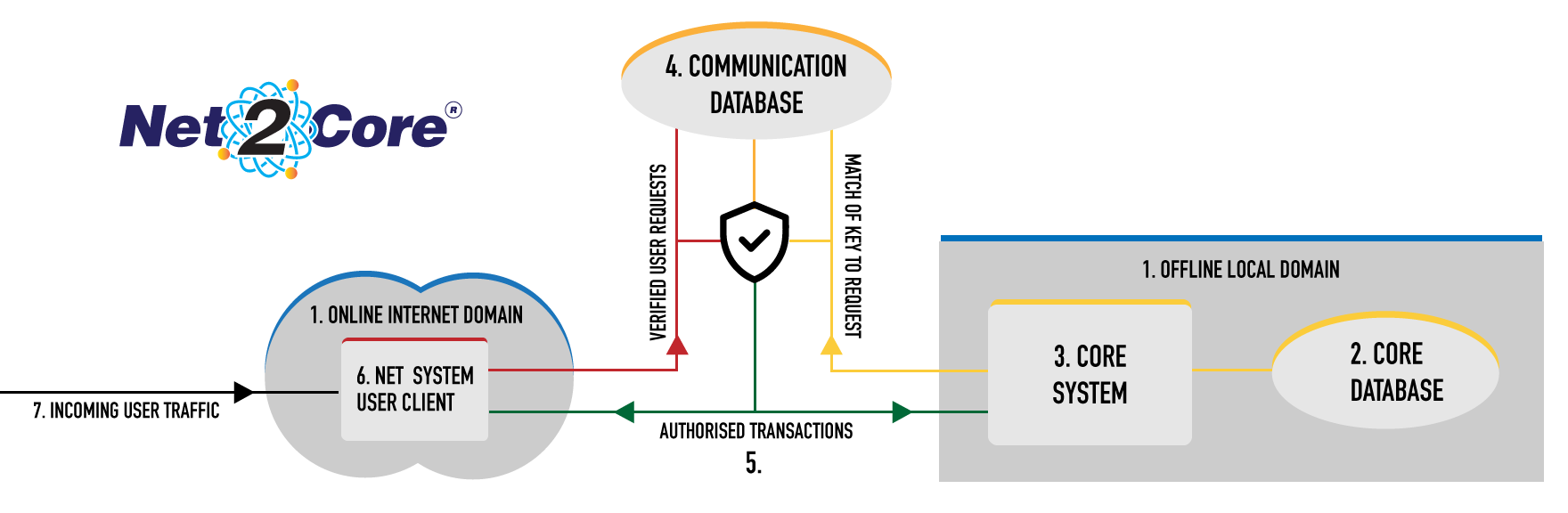
The structure provides security for the data in the Core Database due to its design. Everything contributes to providing Cyber-Security for your data:
The system is separated into two “Domains”. The Local Domain should not be accessible through the Internet. It can be placed in any environment that can be connected to the Internet Domain and the Net Database: e.g. via a LAN to a separate computer.
The Core Database holds all the protected data. It should have all the usual protection applied: e.g. Encryption, Password.
The Core System provides the ONLY path to the Core Database. It should be a compiled program. Compiled programs are difficult to decipher, hence access to the Core Database becomes harder.
The Communication Database contains the request to be processed by the Core system and the results from that processing. Both request and results are held transiently and are deleted as soon as retrieved by the Core or Net System as appropriate: see 7 below as well. This database also has the usual protection applied and can be placed in either the Net Domain or the Core Domain.
The Core system is only operational when initiated by the Net System. This initiation provides the access key required to retrieve the request from the Communication Database. Initiation and Request must match at the same time, which is very difficult to reproduce.
The Net System in the Internet Domain is the only interface directly accessible to the User. It is a Client/Server application. Access to it can be protected by the usual Login, Password or Terminal recognition methods, or in less conventional ways: please refer to GateWay for more detail.
The whole Net2Core® structure is consistent in its transient existence. Each User has a unique copy of the Net System Client/Server process. The Server process only exists for the User while processing a request from the Client. When required the Server will cause a specific copy of the Core System to be loaded. When the Core System concludes its process it will notify the Net System and unload.
We believe that security should be a top priority, not something tacked-on post development or handled by a middle man. All ENIGMA products operate as Client/Server applications. Our Net2Core® structure provides Inherent Cyber-Security within the generated application.
If Internet access to the application through a browser is required, the implementation can use our access controller GateWay to provide increased protection.


The best way to predict the future is to create it.
Abraham Lincoln

All content of this website is under copyright of Parametric Systems (c) | All Rights Reserved
Our mission is the advancement of Application Development and Programming Automation
Website Developed and Managed by
The Stavridis Group Digital Marketing